Description
OSCP+ AD set v1 detailed writeup
Updated in October 2025
Creds given by OffSec
Username: r.adrews
Password: BusyOfficeWorker890
Initial access 192.168.x.206
Pivot to 172.16.x.200 with Chisel or Ligolo-ng
Enumerate the users : $ impacket-GetADUsers -all oscp.exam/r.andrews:BusyofficeWorker890 -dc-ip 172.16.x.200
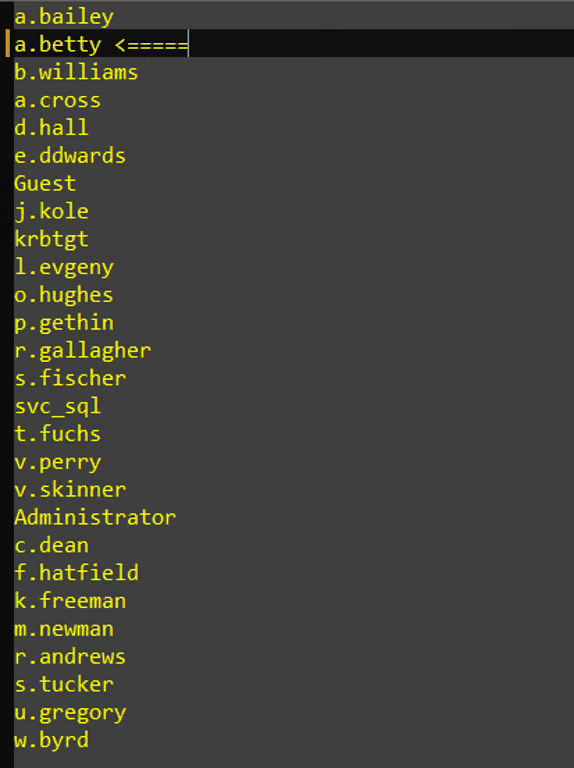
If the " a.betty " user is present, this is the AD set you are looking for
Do not buy it if you are not sure, contact me on Discord or Telegram
No refund is available if you are buying the wrong one !!!
Purchase latest Offensive Security OSCP+ AD set v1 writeup from heldge.store
Contact me on Discord or Telegram if you have any issues with the order.
Discord: @heldge.store
Telegram: @heldge





Verified Purchase –
The seller was responsive and helped me pass the exam with ease!
Verified Purchase (verified owner) –
Order solved I received the file